Darktrace Acquired by Private Equity Firm Thoma Bravo in $5 Billion Deal
What is Vishing? Definition, Examples, Prevention

When was the last time you spent a day without your phone? Chances are you can’t remember. Though our smart devices are a connection to the world they also make you a target for cybercriminals who exploit vulnerabilities through vishing scams.
In this article, we’ll explore vishing, explain the difference between smishing and vishing, and teach you how to prevent vishing.
What is Vishing?
Vishing, short for "voice phishing," is a type of social engineering attack that uses phone calls or voicemails to trick victims into revealing personal information.
Bad actors use vishing to steal personal information that can be used for identity theft or financial fraud. Once they have login credentials, attackers can hijack email accounts, bank accounts, social media profiles, or even internal company systems. This can be used as a springboard for more sophisticated attacks.
Vishing calls can also be used to trick victims into downloading malicious software onto their devices. This malware could then steal data, spy on activity, or even take control of the device.
Outside of financial gain, vishing is also used to spread disinformation or propaganda. By impersonating trusted sources, attackers can manipulate people's beliefs or actions.
Read: What are Deep Fakes and Why Are They Dangerous?
Attackers may use additional tools including voice altering software and spoof phone numbers to make their scam seem more authentic.
Vishing relies on human vulnerabilities and our tendency to trust and help those in need. This is amplified by cybercriminals who apply pressure to act urgently before victims can properly rationalize what is being asked of them.
Vishing Examples
The “grandparent scam” is the most well-known example of a vishing attack. In the grandparent scam, the malicious actor pretends to be a grandchild of the victim. They might use a stolen name from social media or try to elicit it from the grandparent during the call. The scammer will then create a story about the grandchild being in trouble, such as a fabricated accident, arrest while travelling or needing money to avoid a bad situation.
By emphasizing the urgency of the situation, the victim is pressured to act quickly without thinking it through. They might also plead with the grandparent to keep the situation a secret from other family members. The grandparent scam exploits a grandparent's love and concern for their grandchild by creating a sense of panic and urgency. This emotional manipulation makes it harder for the victim to think clearly and verify the situation before sending money or handing over personal details.
Vishing attacks can bypass even sophisticated cybersecurity measures in large companies by preying on the weakest link in the defences- employees. In 2020, Twitter, now known as ‘X’, was the target of a coordinated social engineering attack. Cybercriminals made vishing calls to Twitter’s employee support lines. They kept their instructions simple: "We need you to reset your password." While some employees flagged the call as suspicious, others were caught off guard. The targeted employees were sent to a replica website designed to steal their information.
We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools.
— Support (@Support) July 16, 2020
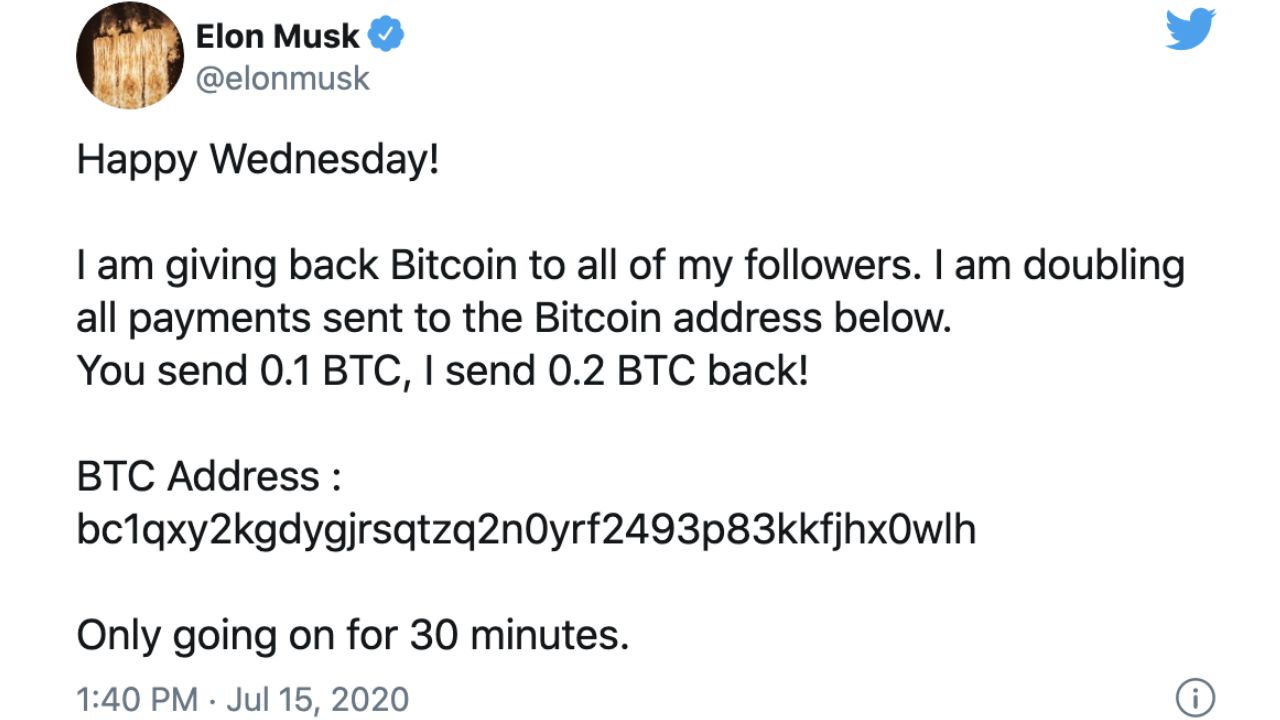
Through this, hackers were able to gain access to celebrity accounts, the first tweet sent from Elon Musk’s account, quickly followed by other high influence accounts including Barack Obama, Joe Biden, Kim Kardashian, Kayne West and Jeff Bezos, as well as major brands including Apple and Uber.
Read: UK Man Admits to Hijacking Top Twitter Accounts for Crypto Scam
The scam tweets promised to double any Bitcoin sent to a specific cryptocurrency wallet as a charitable act. This proved effective quickly. Within minutes, over 320 transactions flooded one of the wallet addresses, totalling over US$110,000 in Bitcoin before Twitter managed to take down the scam messages.
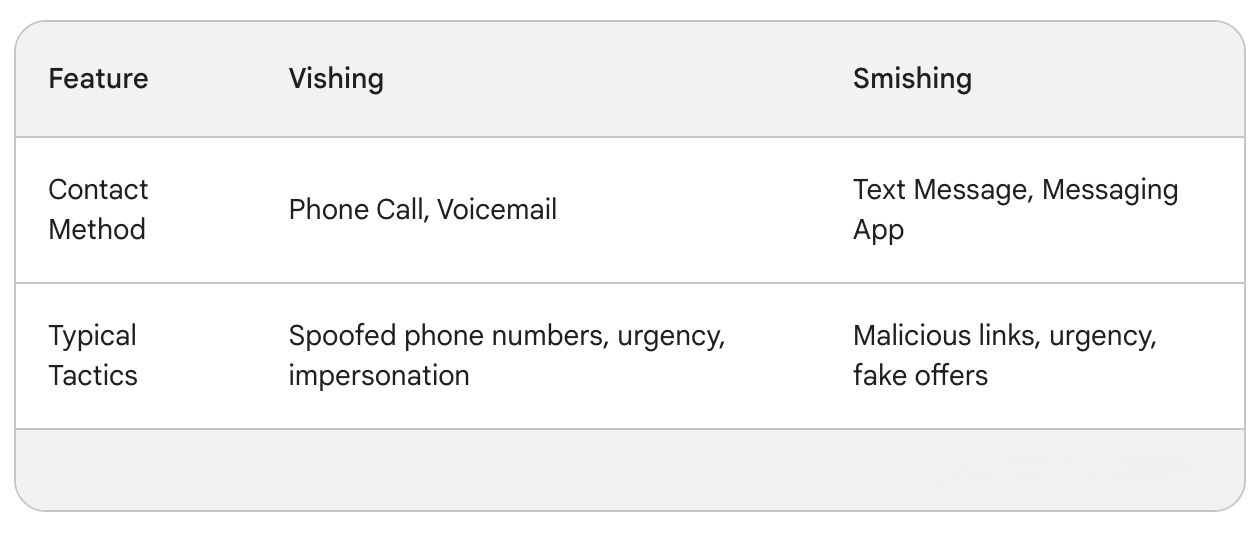
What is the difference between smishing and vishing
The difference between smishing and vishing is that smishing attacks use text (SMS) or app messages whilst vishing uses phone calls or voicemails.
Smishing scams are sent through text messages (SMS) or messaging apps like WhatsApp. The message will usually contain a link that, when clicked, leads to a fake website designed to steal your information or install malware. The message itself might create a sense of urgency or offer a tempting deal to trick you into clicking the link.
Vishing scams use phone calls or voicemails. Scammers usually pretend to be from a trusted organization, creating a sense of urgency to pressure victims into revealing personal details. They might spoof phone numbers or use voice-altering software to increase believability.
How to Prevent Vishing?
Vishing scams can be sophisticated attacks that can happen to anyone, but by following some key steps you can significantly improve your defences.
Be wary of unsolicited calls, especially those creating a sense of urgency. Never share personal information over the phone, and if the caller claims to represent a legitimate organization, verify the information independently using a trusted source, not a phone number provided in the call.
Utilize strong passwords and multi-factor authentication to further secure your accounts from being compromised.
Educate older relatives to help them avoid being a victim of a “grandparent scam”, by taking time to explain the common tricks scammers use and how to identify red flags. Emphasize the importance of hanging up before taking any action. Encourage them to call you or another trusted family member to verify the story directly with the grandchild even if they have been asked to keep it a secret.
Businesses are a prime target for vishing scams due to the potential for hefty financial losses or stolen data. To fortify your defenses, prioritize employee education. Regular training on vishing tactics, red flags, and proper response protocols equips them to identify suspicious calls as well as simulations and phishing tests to put this into practice. Using a multi-layered approach that combines employee awareness, technical security measures, and clear communication practices, businesses can significantly reduce the risk of falling victim to vishing attacks.