What is a Botnet? Definition, Examples, How To Prevent
What is Pretexting and How Can You Defend Against it?

Keeping yourself secure online has never been more challenging in today’s cyber threat landscape. Recent research by IT Governance revealed that in March 2024 alone there were 3,478 publicly disclosed security incidents and a whopping 299,368,075 records known to be breached worldwide.
Whether it is the surging number of data breaches or the rise of sophisticated phishing campaigns powered by large language models (LLMs), individuals and organisations alike today have more risks to worry about than ever before.
One of these risks is pretexting, which has become an increasingly prevalent attack method used by hackers looking to steal sensitive information or compromise critical IT systems.
This article tells you everything you need to know about pretexting, including what it is and how to identify and protect yourself against it.
What is Pretexting?
Pretexting is a type of social engineering attack where the scammer makes up a believable story, or pretext, to gain your trust. Once they have you trusting them, they'll try to get you to reveal sensitive information, like your account passwords or Social Security number.
First, the scammer will come up with a fake scenario. They might pretend to be from your bank, your credit card company, the tech support department at your work, or even law enforcement. This can be done over the phone, email, text message, or even in person. The attacker will often try to sound friendly and helpful to make you feel comfortable.
They'll then use this fake story to try to get you to do something, like give them your personal information, click on a malicious link, or send them money.
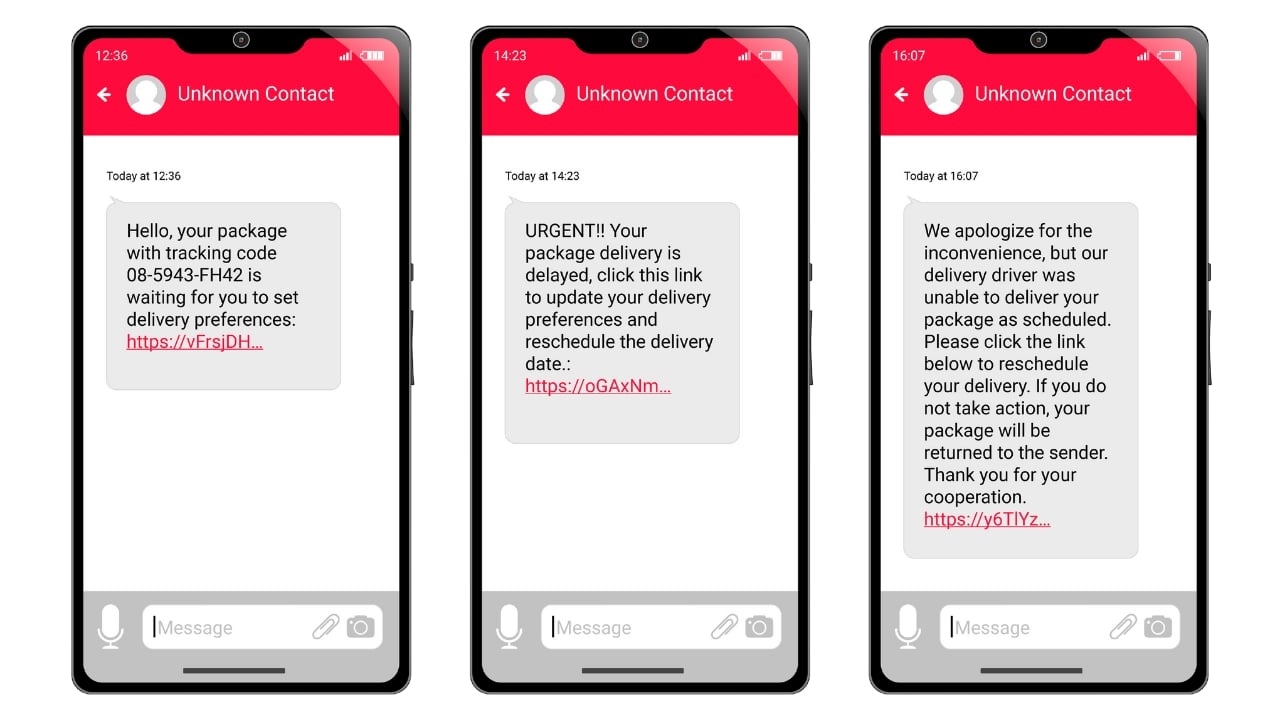
Pretexting is successful because it preys on people's natural tendency to be helpful and trusting. By creating a believable scenario, the scammer can make you think you're doing the right thing by giving them the information they're asking for.
To make their character impersonations and situations believable, the scammer will typically research and gather information about their targets online before contacting them. This is not as difficult as you might think.
According to a report from Omdia, hackers can craft a convincing story, based on information from social media feeds and other public sources, after just 100 minutes of browsing Google.
Other techniques for making characters more believable include spoofing the character’s email address or phone number, or gaining outright unauthorized access to the character’s actual email account or phone number and using it to send the message.
Examples of Pretexting
Pretexting scammers come up with all sorts of stories to manipulate you into revealing sensitive information. Here are some of the most common examples of pretexting watch out for:
1. Fake Tech Support scam
Fake tech support is a well-known example of pretexting where a scammer pretends to be a representative from a well-known tech company like Microsoft or Apple.
They'll claim to have detected a problem with your computer, like a virus or outdated software, with the goal of gaining your trust and convincing you to give them remote access to your device or pay for unnecessary services. Once they have access, they can steal personal information, install malware, or even lock you out of your own computer and demand a ransom.
All these elements fit the classic pretexting strategy: creating a believable story (pretext) to manipulate you into compromising your security. Fake Tech Support scams are a common way for attackers to steal information and money.
2. Phishing with a Pretext
Phishing emails or calls often use a pretext, a fabricated story or scenario, to gain the victim's trust. This could be the "urgent account verification" scenario in a bank phishing attempt, or the "you won a prize" story in a lottery scam.
The email might warn you about suspicious activity on your account or ask you to verify your information. But the link in the email takes you to a fake website designed to steal your login credentials. By creating a believable scenario, the pretext makes the victim more likely to believe the phishing attempt is legitimate.
Not all phishing attacks use pretexting, but it's a powerful tool in a scammer's arsenal. Many phishing attacks today also rely on AI tools such as dark LLMs to generate believable emails and texts that are free of typos and replicate legitimate contacts.
Not all phishing attacks are over text or email though. Vishing attaks, also known as voice phishing over the phone, are also become increasingly common and often rely on a pretext to gain information from their target,
3. The "Urgent Family Emergency"
The "Urgent Family Emergency" scam is a classic example of pretexting. It uses a fabricated scenario to gain your trust and steal your personal information or money.
A scammer calls you pretending to be a law enforcement officer, hospital worker, or someone else claiming a relative of yours is in trouble and needs money right away. This is a common tactic to pressure you into sending cash or giving out your financial information.
4. The "You Won!" Scam
In the “you won!” scam, The scammer creates a fabricated situation where you supposedly won a prize or lottery. This is the pretext, a believable story to gain your trust.
The goal is to get you to reveal personal information or take an action that benefits them. This could be sharing your credit card details to "claim" the prize, or clicking on a malicious link that steals your data.
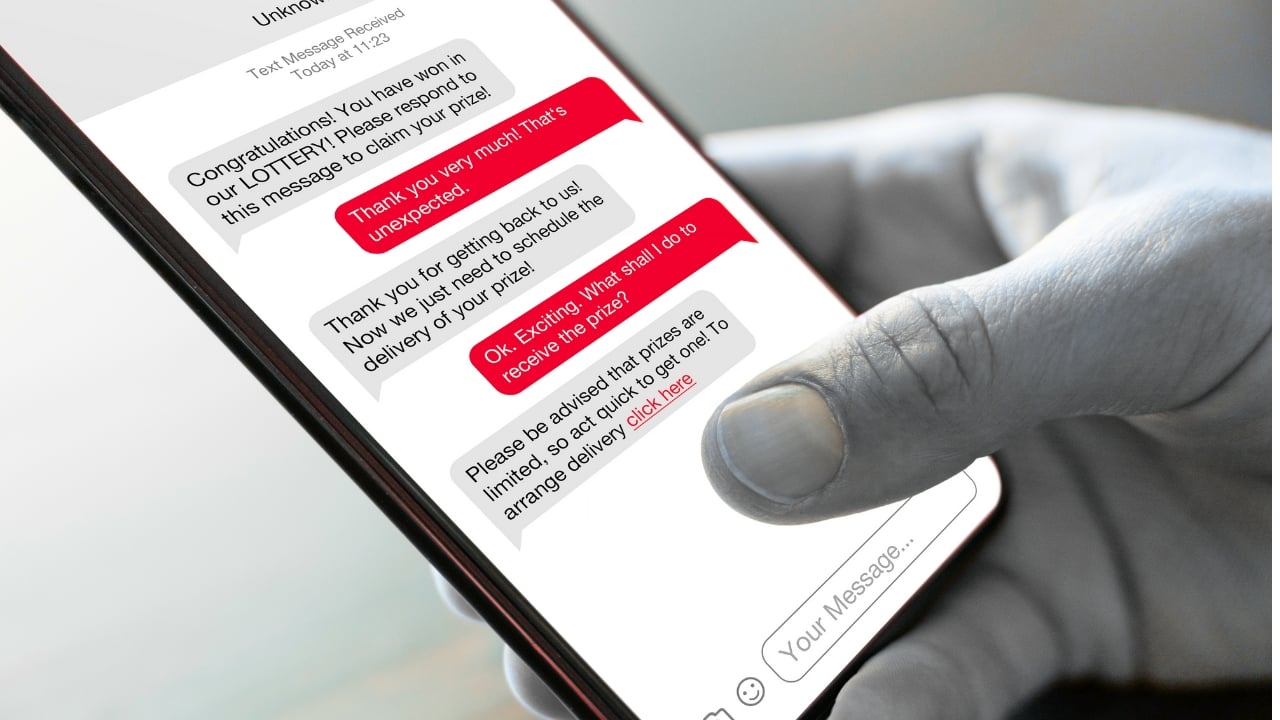
The "You Won!" scam uses the allure of a reward to manipulate your emotions and trick you into giving away valuable information or money. It perfectly fits the definition of pretexting.
5. Business email compromise (BEC) scams
In BEC, attackers create a believable scenario, or pretext, to trick the victim into trusting them. This pretext typically involves impersonating a legitimate source, like a colleague, CEO, vendor, or other trusted contact within a company. The pretext often involves a sense of urgency or appeals to the familiarity of the sender to pressure the victim into taking action, such as authorizing a wire transfer or sending sensitive information.
Remember, pretexting can be very believable. The key is to be suspicious of unsolicited calls, emails, and texts, especially those that create a sense of urgency or ask for personal information.
Identifying pretexting attacks
Pretexting scammers create fake situations to steal your personal information. This can be tricky to identify because they rely on creating a believable scenario and manipulating trust.
Here are some key characteristics and red flags to look out for pretexting:
Common communication characteristics
- Unsolicited contact. Be wary of calls, emails, texts, or even physical interactions you didn't initiate, especially from someone claiming to represent a legitimate organization.
- Sense of urgency. Pretexting attackers often try to pressure you into acting quickly by creating a sense of urgency or crisis. They might claim your account is compromised, there's a problem with your device, or you need to take immediate action to avoid negative consequences.
- Inconsistent information. Pay attention to details in their story. Does it sound logical? Are there inconsistencies in their claims or the information they provide?
- Suspicious sender/caller information. Look out for obvious red flags like email addresses with misspellings or phone numbers that don't match the organization they claim to represent.
Comment request characteristics
- Requests for personal information. Legitimate organizations rarely ask for sensitive information like passwords or Social Security numbers through unsolicited communication.
- Pressure to pay upfront. Be wary of anyone requesting immediate payment, especially for services you didn't request.
- Unusual requests. If someone asks you to do something out of the ordinary, like downloading software or granting remote access to your device, be suspicious.
By being aware of these red flags and staying cautious, you can significantly reduce your risk of falling victim to a pretexting attack. Remember, if something sounds too good to be true, it probably is.
Defending Against Pretexting
To protect yourself against pretexting, it's important to treat any unexpected call, email, text, or even in-person interaction with suspicion, especially if they involve requests for personal information or urgent action.
Don't rely on the information provided in the initial contact. If someone claims to be from a bank, credit card company, or any other organization, verify their identity independently. Here's how:
- Look for contact information from a trusted source. Don't use phone numbers or website links provided in the suspicious message. Find the official contact details on the organization's verified website or a phone book.
- Call the official number. Reach out to the organization directly using the verified phone number and explain the situation. They can confirm the legitimacy of the contact and the supposed issue.
Make it a habit to never share sensitive information like passwords, Social Security numbers, account details, or even your date of birth unless you're absolutely certain who you're interacting with. It's also important to keep your software updated with the latest security patches, especially on devices you use for financial transactions or accessing sensitive information. Many organizations use a password manager to create strong, unique passwords for all your accounts.
If you suspect a pretexting attempt, report it to the organization being impersonated. You can also consider filing a complaint with the Federal Trade Commission (FTC) to help them track and prevent these scams.
By following these steps and staying vigilant, you can significantly reduce your risk of falling victim to a pretexting attack. Remember, it's always better to be safe than sorry. If something feels suspicious, take the time to verify and don't hesitate to walk away from the situation.