
Non-human identities (NHIs) such as Application Programming Interface (API) keys, service accounts, and machine certificates are very important in today’s IT landscape. They help with DevOps automation, make machine-to-machine connections secure, and support business processes in hybrid and multi-cloud environments.
These digital identities often work quietly in the background with access to systems, applications, and sensitive data. This makes it harder to monitor and control. If not managed well, they can cause serious security, compliance, and operational problems.
That’s why managing the entire lifecycle of NHIs from creation and use to rotation and retirement is crucial to prevent privilege creep, credential misuse, and unauthorised access.
By treating NHIs as an integral part of the identity system and applying consistent security policies, governance, and automation, organisations can maintain visibility and control over these identities. This approach strengthens security and compliance while enabling the business to remain agile and responsive.
5 Critical Stages in the Non-Human Identity Lifecycle
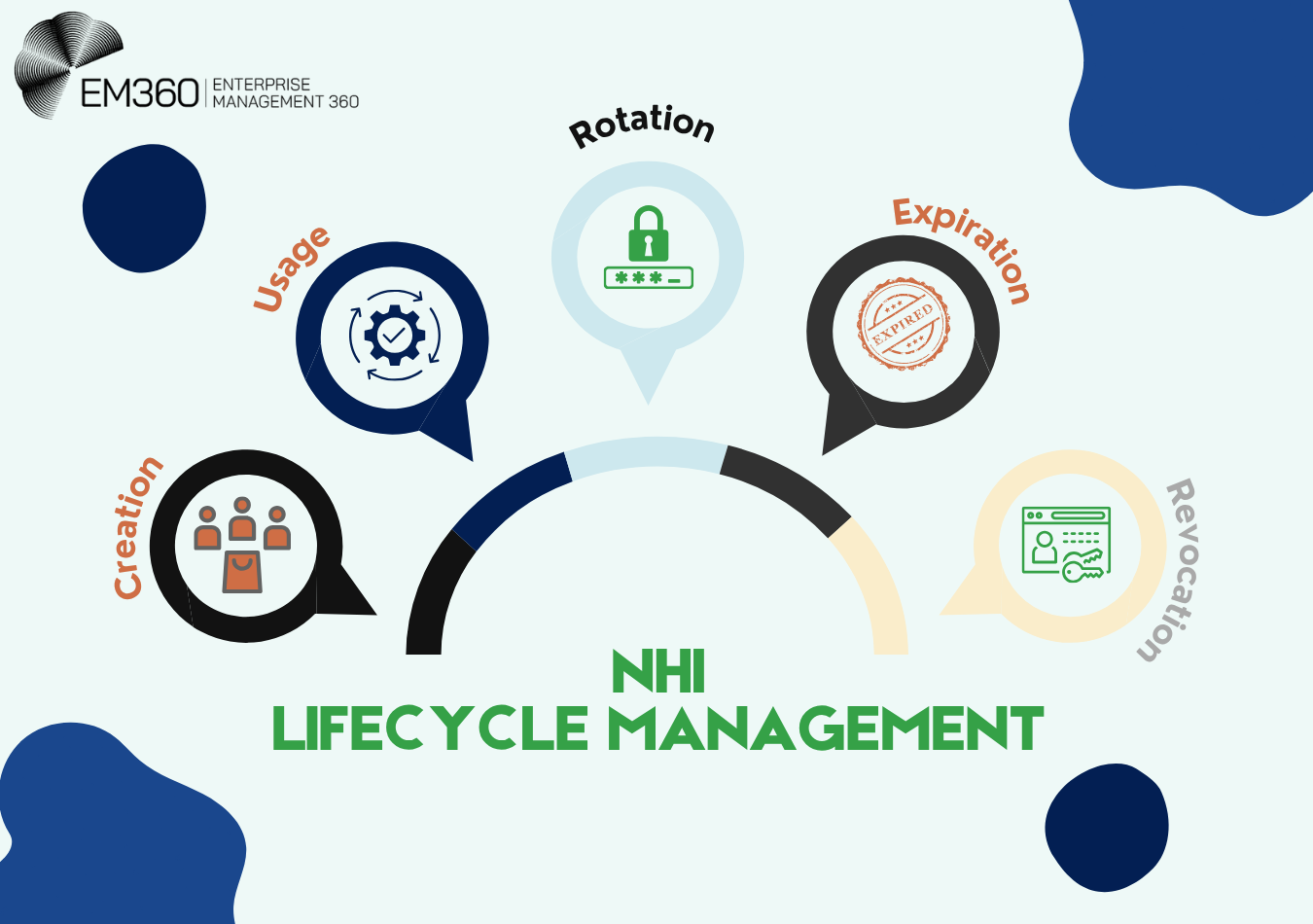
Managing non-human identities (NHIs) isn’t as simple as it seems. From service accounts and machine identities to IoT devices and APIs, these digital entities must be tightly controlled across five critical stages: creation, usage, rotation, expiration, and revocation. Each stage is essential for maintaining strong security and compliance in the technology we use today.
Here’s what you need to know:
Creation
The creation stage involves defining each non-human identity’s unique attributes, roles, and permissions. This step includes registering the entity within an identity management system and assigning a digital identity that reflects its purpose and access scope. To ensure accuracy and security, organisations use identity and access management (IAM) platforms, automated provisioning tools, and APIs. These technologies simplify and standardise the onboarding of non-human identities.
Usage
Once created, non-human identities are actively used to perform automated tasks or access systems as intended. Monitoring their usage ensures they operate within defined permissions and detects any abnormal or unauthorised activity. During this phase, it's important to maintain appropriate access rights and update identity attributes as operational needs evolve, keeping the identities aligned with the company’s security policies.
Rotation
Regularly rotating credentials such as passwords, certificates, or keys reduces the risk of compromise. This process ensures non-human identities remain secure by limiting the lifespan of any single credential. Rotation can be automated using identity management tools to enforce policies that trigger credential updates at certain intervals or after specific events.
Expiration
Non-human identities and their credentials should have clear expiration dates based on their intended use. Expiration limits the window of exposure if credentials are forgotten or overlooked. Systems should notify administrators when identities or credentials approach expiration and automatically disable or deactivate them once expired.
Revocation
Revocation is the formal process of removing non-human identities from active use. This includes disabling access, deleting credentials, and cleaning up configurations to prevent any further authentication. During revocation, organisations must follow data retention policies and privacy regulations to securely archive or delete any associated data, ensuring compliance and minimising security risks.
Why is the NHI Lifecycle Important?
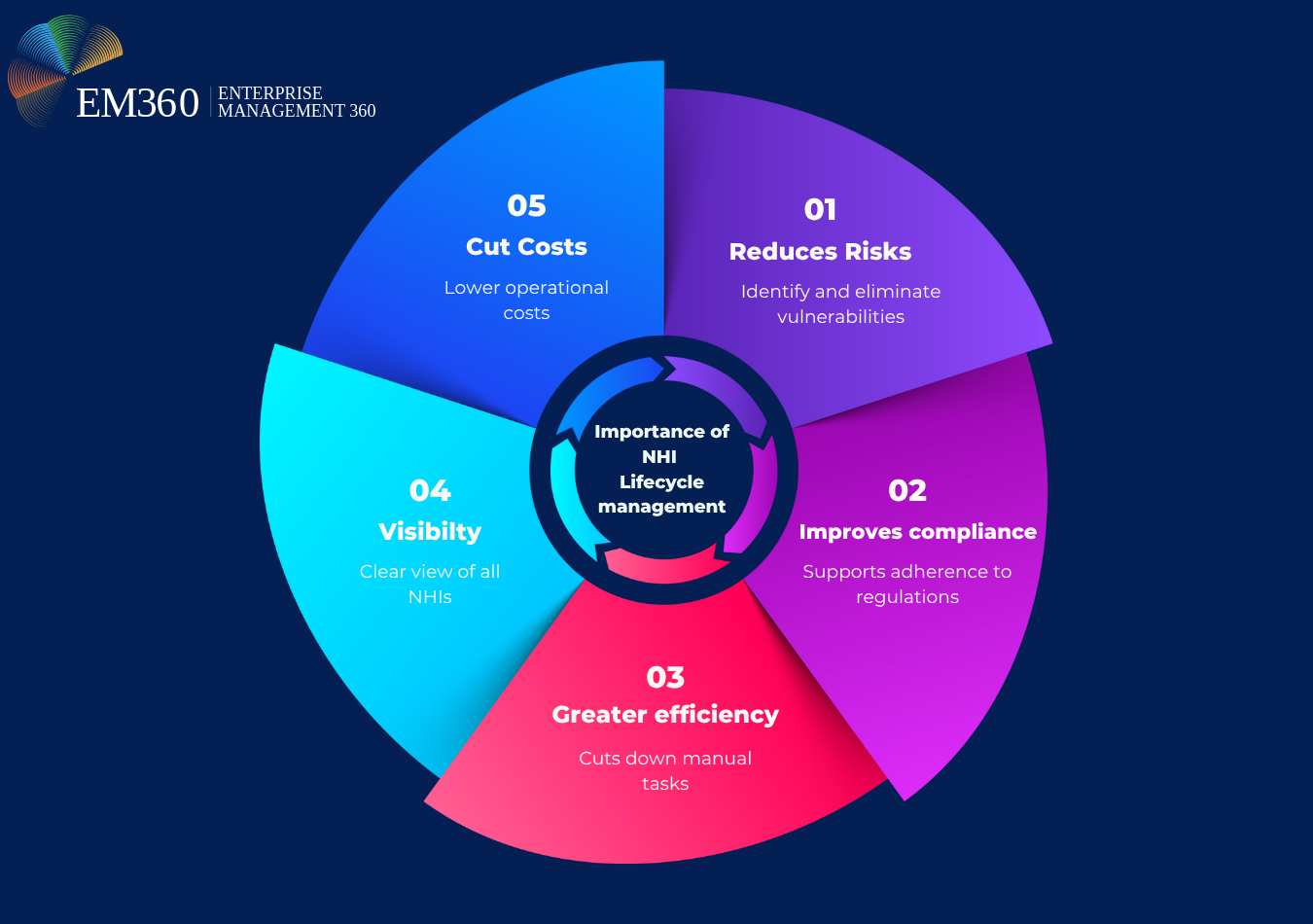
Effective management of non-human identities (NHIs) involves overseeing every stage from creation to deactivation and everything in between. Each step, whether assigning permissions or auditing usage, carries important security considerations.
Adopting an approach to NHI lifecycle management is important because:
- Risk reduction: Strong lifecycle management helps identify and eliminate vulnerabilities, lowering the chances of data breaches. Protecting both NHIs (“the users”) and their access credentials (the keys), along with continuous behaviour monitoring, safeguards critical assets.
- Improved compliance: Managing NHIs systematically supports adherence to regulations like GDPR, HIPAA, and PCI DSS by enforcing policies and maintaining detailed audit logs, simplifying regulatory requirements.
- Greater efficiency: Automation cuts down manual tasks involved in handling NHIs and their secrets, allowing security teams to focus on higher-value projects. Automated rotation of credentials and timely decommissioning make routine processes smoother.
- Better visibility and control: Centralising access management provides a clear view of all NHIs, their credentials, and permissions, enabling tighter governance and quicker response to risks.
- Cost savings: Streamlined workflows and reduced manual oversight help lower operational costs, making NHI management more economical.
Frameworks and Tools for Governance and Automation
Once you have mapped your organisational perimeter and understood the scope of your non-human identities (NHIs), the next step is to establish a strong policy framework with clear priorities.
This framework should define how NHIs are accessed, attested, rotated, federated, and ultimately decommissioned. Adopting least-privilege access for all NHIs and automating critical tasks like secret rotation, recertification, and auditing is key to maintaining security and compliance.
To ensure policies are not just well-intentioned but actively enforced, automation plays a major role. Automating policy enforcement reduces manual oversight and human error, promoting consistency and reliability across your NHI management practices.
The automation workflows typically handle routine, repetitive tasks such as credential rotation, permission updates, and health checks. These workflows integrate tightly with existing infrastructure and developer pipelines. For example, automatically rotating credentials and updating permissions whenever an application is redeployed through an infrastructure-as-code pipeline..
Identity and Access Management (IAM) platforms handle provisioning, while secrets management tools securely store credentials such as API keys, passwords, and certificates. Monitoring systems continuously observe NHI behaviour. Together, these solutions create a self-sustaining ecosystem in which routine security tasks are automated, freeing security teams to focus on more strategic priorities.

Popular frameworks and tools
- Identity governance and administration (IGA): Focuses on managing identity lifecycles, policy enforcement, and compliance reporting. IGA tools provide visibility into who or what has access and help streamline certification and attestation processes. It also helps organisations comply with a variety of government and industry regulations and architectures, like data privacy mandates.
- Privileged access management (PAM): Specialises in securing and controlling access to privileged accounts, including non-human identities with elevated permissions. PAM solutions offer session monitoring, credential vaulting, and just-in-time access to reduce risk. Two primary use cases for privileged access management are preventing credential theft and achieving compliance.
- Cloud infrastructure entitlement management (CIEM): Targets the specific challenges of managing permissions in cloud environments. CIEM tools help discover, analyse, and remediate excessive permissions and enforce least-privilege access in cloud-native contexts. The purpose of CIEM is to understand which access entitlements exist across cloud and multicloud environments, and then identify and mitigate risks resulting from entitlements that grant a higher level of access than they should.
Tools in the NHI market
- One Identity: Offers comprehensive IGA and PAM capabilities that streamline identity management and secure privileged access across hybrid environments. One Identity offers organisations solutions for rapid discovery and onboarding of assets, automated workflow engines, remote password approval, full REST API integration, and even a free personal password vault for business users.
- Entro Security: This solution offers intelligent automation and governance for both human and non-human identities, emphasising risk reduction and operational efficiency. It automatically scans an organisation's infrastructure to identify and inventory bots, service accounts, API keys, certificates, tokens, and other secrets. This platform manages the entire non-human identity lifecycle—handling discovery, classification, posture management, automated operations, and threat response seamlessly.
- Astrix: This platform is renowned for simplifying workflows and enhancing data integration, delivering increased efficiency through automation and powerful analytics. Its intuitive interface and extensive customisation options make it adaptable to a wide range of industries. By fostering better collaboration and enabling data-driven decision-making, Astrix helps organisations boost productivity and achieve smarter outcomes.
- Oasis: This purpose-built solution for managing non-human identities (NHI) brings together advanced capabilities for discovery, posture analytics, and real-time anomaly and threat detection. It helps organisations identify and classify non-human identities across their environments, assess their security posture, and detect suspicious or risky activity. Combined with efficient remediation workflows and complete lifecycle management, this approach supports a secure, consistent, and scalable way to govern non-human identities, reducing risk while maintaining operational agility.
How do these tools improve efficiency?
By leveraging these frameworks and tools, organisations can:
- Automate complex processes like secret rotation, permission updates, and compliance attestation.
- Improve security posture by enforcing least-privilege policies and reducing human error.
- Gain centralised visibility into non-human identity usage across diverse environments.
- Integrate seamlessly with existing infrastructure, including CI/CD pipelines, cloud platforms, and security monitoring systems.
- Free up security teams to focus on strategic initiatives rather than routine maintenance.
A tip for any organisation is to focus on automating their NHI management strategy to help improve efficiency, apply security policies consistently, and reduce manual work for teams. Automation also helps strengthen identity management, making it more reliable and better prepared to handle any security threats.
Pain Points of Non-Human Identity Lifecycles

Non-human identities (NHIs) — such as service accounts, bots, and machine credentials — pose unique challenges that go far beyond traditional identity management. Security teams commonly face many major obstacles:
Discovery and inventory
Unlike human identities, NHIs are scattered across vaults, code repositories, messaging tools, and cloud platforms. This fragmentation makes it extremely difficult to maintain an accurate, up-to-date inventory. Without a clear understanding of where NHIs live and what permissions they hold, identifying risks or fixing misconfigurations becomes nearly impossible.
Business dependency
Organisations depend on NHIs to automate workflows, connect applications, and maintain seamless operations. Security teams often hesitate to disable or rotate a credential if they don’t fully understand its use, fearing they might break critical business processes. This fear of disrupting operations frequently leads to inaction, leaving risky credentials untouched.
Limited visibility
NHIs operate across cloud environments, CI/CD pipelines, and DevOps workflows. Without centralised oversight, identities that exist but aren’t tracked or monitored emerge. Without a complete picture, it’s hard to know what access these identities have or to apply proper controls.
Privilege creep
Many NHIs are granted broad, persistent permissions that rarely get reviewed. Over time, these privileges accumulate, a problem known as privilege creep, expanding the attack surface. If attackers compromise such overprivileged identities, they can escalate their access across systems.
Weak secrets management
NHIs rely on API keys, tokens, and certificates to authenticate. But these secrets often end up hardcoded, stored in plaintext, or exposed in repositories — leading to what’s called secrets management. Attackers actively target these weak points to breach systems and move laterally across environments.
Lack of lifecycle governance
Developers frequently create NHIs for temporary tasks but fail to properly decommission them when they’re no longer needed. Without automated lifecycle controls, these orphaned NHIs become hidden entry points that attackers can exploit.
Absence of traditional security controls
NHIs cannot use security methods designed for humans, such as multi-factor authentication or user behaviour monitoring. Instead, they rely on policies like least privilege, continuous monitoring, and automated credential rotation. Without these measures, NHIs remain highly vulnerable.
Orphaned identities
An orphaned non-human identity (NHI) refers to an identity that remains active with permissions but is no longer in use. These stale NHIs often result from changes in business operations, such as ending relationships with third-party vendors, organisational shifts like employee departures or role changes, or technological updates like retiring an application.
A frequent issue uncovered in security reviews is the presence of unused NHIs tied to discontinued SaaS applications, often used for one-off tasks like data migration. Once these tasks are finished, such applications and their associated identities are frequently overlooked, remaining active without proper deactivation. These dormant identities pose significant security risks by expanding the attack surface and potentially acting as undetected entry points for attackers..
Best Practices for Managing Non-Human Identities (NHIs) at Scale
As organisations grow more reliant on automation, cloud, and distributed architectures, non-human identities (NHIs) have multiplied rapidly. These identities representing applications, workloads, and services often outnumber human accounts, yet are rarely managed with the same thoroughness. Without proper controls, NHIs can create hidden risks that threaten security and compliance. To address this challenge, consider a practical three-step approach to bring order and consistency to your NHI strategy.
Let's take a look:
Step 1: Gain visibility
Start by building a complete inventory of all non-human identities across your environment. This will help reveal blind spots and provide a clear view of which identities exist, what they do, and how critical they are.
It’s also vital to monitor certificate status, tracking expiration dates and verifying cryptographic algorithms are up to date to keep your organisation maintaining a solid overall level of security across your systems, processes, and policies
Step 2: Select the right NHIM tool
Choosing a suitable non-human identity management (NHIM) solution is key to long-term success. Select a platform that can support the risks and priorities identified in your initial assessment, and that can operate across cloud, on-premises, or hybrid environments. Look for capabilities such as:
- Identity discovery and ownership assignment: Clearly define who is responsible for each identity.
- Attestation and lifecycle management: Ensure periodic review and updates.
- Automatic remediation: Fix misconfigurations without manual intervention.
- Centralised management: Unify NHI visibility across SaaS, cloud, and on-prem environments to enforce consistent controls and reduce credential sprawl.
- Least privilege enforcement: Grant only the minimal permissions needed to lower the risk of lateral movement.
- Real-time monitoring: Detect suspicious activity early and trigger automated responses.
- Zero trust principles: Continuously validate every identity to avoid implicit trust, even if credentials are compromised.
- Ephemeral credentials: Replace static secrets with short-lived, auto-expiring certificates to limit exposure.
For hybrid or complex environments, ensure the tool integrates smoothly with your existing IAM, PAM, and security systems so you can scale and adapt as your organisation grows. Context leads to action, choose a solution that not only discovers identities but also helps you act on what you find.
Step 3: Automate and enforce controls
Given the sheer volume of non-human identities, automation is important. Once you have visibility, use automation to provision, renew, and revoke credentials as needed. This supports crypto-agility, making it easier to transition to stronger cryptographic standards, including post-quantum algorithms, at scale.
Establish clear enterprise-wide policies aligned with evolving standards such as NIST, NIS2, and PCI-DSS to maintain secure cryptographic practices. Staying ahead of developments in post-quantum cryptography will ensure you are ready for potentially disruptive shifts in encryption requirements.
Real NHI Case Studies
These recent real-world incidents illustrate why managing the full lifecycle of non-human identities is so critical. The following case studies demonstrate how lapses in controlling API keys and other machine credentials can be exploited, leading to severe security breaches.
By studying these examples, organisations can better understand the consequences of weak lifecycle management and see why proactive, automated, and robust controls are essential for protecting non-human identities in today’s threat landscape
Microsoft Azure OpenAI Service targeted by Hacking-as-a-Service Group
In December 2024, Microsoft took legal action against a Hacking-as-a-Service (HaaS) group that exploited vulnerabilities in its Azure OpenAI services. The attackers used stolen Azure API keys along with custom software to bypass AI safety and filtering mechanisms, allowing them to generate harmful and illegal content at scale.
This incident underscores the increasing threat of cybercriminals using AI technologies and highlights the need for stronger security measures in the evolving field of generative AI. The group’s operation involved a combination of stolen credentials, advanced circumvention techniques, and obfuscation tactics to evade Microsoft’s protections.
In response, Microsoft acted quickly, employing both legal and technical measures to dismantle the threat and strengthen defences against future attacks.
BeyondTrust breach linked to US Treasury cyber incident
BeyondTrust, a cybersecurity provider specialising in Privileged Access Management (PAM) and Secure Remote Access, detected unusual activity affecting some customer instances of its Remote Support SaaS platform back in December 2024. An investigation confirmed that a compromised API key had been used to gain unauthorised access, with the potential to escalate attacks in customer environments.
BeyondTrust revoked the key, notified affected customers, and suspended impacted systems by December 5. Later, on December 30, 2024, the US Treasury announced a major incident linked to this breach, reporting that its systems had been accessed, including employee workstations and some unclassified documents.
This breach was confirmed on December 5, 2024, prompting BeyondTrust to revoke the compromised API key, notify affected customers, and suspend the impacted instances.
The New York Times breach
In June 2024, the New York Times (NYT), known for its journalistic excellence, made headlines for a different reason: a cybersecurity breach. The incident stemmed from an exposed GitHub access token, which allowed an attacker to steal 270GB of data, including internal source code. The stolen data later surfaced on public platforms such as 4chan, bringing the breach to light.
The breach began when a GitHub token was accidentally exposed, likely due to poor credential storage or placement in a public repository. With the token’s broad access permissions, the attacker was able to access roughly 5,000 repositories and extract 270GB of sensitive data.
The New York Times identified and responded to the breach in January 2024 by revoking the exposed credentials and starting an internal investigation. However, details of the incident were not made public until June 2024, raising concerns about the delay in disclosure.
Managing non-human identities is no longer optional in today’s complex digital environments. Organisations should start strengthening their processes to protect their organisation from the growing wave of cyber threats.
Strengthening Security by Managing Non-Human Identities
Non-human identities such as AI agents, automated scripts, and machine accounts are essential parts of digital operations but bring unique security challenges. Managing these identities requires a good understanding of their interconnected nature, lifecycle stages, and specific security needs.
Success for any organisation depends on recognising NHIs not as isolated elements but as part of a larger ecosystem where every identity must be securely monitored and properly governed to other systems.
By implementing strong lifecycle management, automation frameworks, and security controls, organisations can effectively handle their growing number of non-human identities while maintaining both security and compliance. Adopting this holistic approach is key to reducing risks and building resilient cybersecurity defences.













Comments ( 0 )