
Non-human identities (NHIs) are multiplying faster than most organisations can track. According to industry estimates, they already outnumber human identities by as much as 92 to 1 — and that ratio is still climbing.
These digital identities are the backbone of everything from DevOps automation to machine-to-machine authentication in hybrid environments. And they include everything from API keys in cloud services to service accounts that support CI/CD pipelines.
But what makes them necessary also makes them dangerous. They work quietly in the background, often without any kind of traditional monitoring or control. And because there are so many of them, security teams tend to forget about them, give them too much access, or don't see them at all.
As businesses accelerate cloud adoption and layer in automation, artificial intelligence, and infrastructure as code, the identity landscape is becoming increasingly complex — and increasingly exposed.
So what exactly are non-human identities, and why are they fast becoming one of the most urgent blind spots in enterprise cybersecurity?
What Is a Non-Human Identity?
Digital transformation doesn’t just scale systems — it multiplies the identities within them. And as enterprise IT environments become more automated, distributed, and cloud-native, identity itself is evolving.
Organisations no longer manage access for people alone. They now have to account for thousands, sometimes millions, of digital entities that run scripts, connect services, and execute critical operations behind the scenes.
Definition and core function
A non-human identity is a type of digital entity used by software applications, systems, or devices to authenticate, communicate, and perform tasks without direct human involvement. Human users log in with things like passwords, biometrics, or multi-factor authentication (MFA), then interact with each platform or apps interface.
NHIs, on the other hand, work autonomously and their credentials are tokens, digital certificates, or service accounts. These act as the passports that allow them to access resources through APIs, automation workflows, and other means.
As risky as they may be, these identities are an essential part of access management (IAM) in modern infrastructure. They make seamless system-to-system interaction possible, so that cloud services, DevOps pipelines, and machine-based processes can all function securely and efficiently.
Examples of NHIs in Action
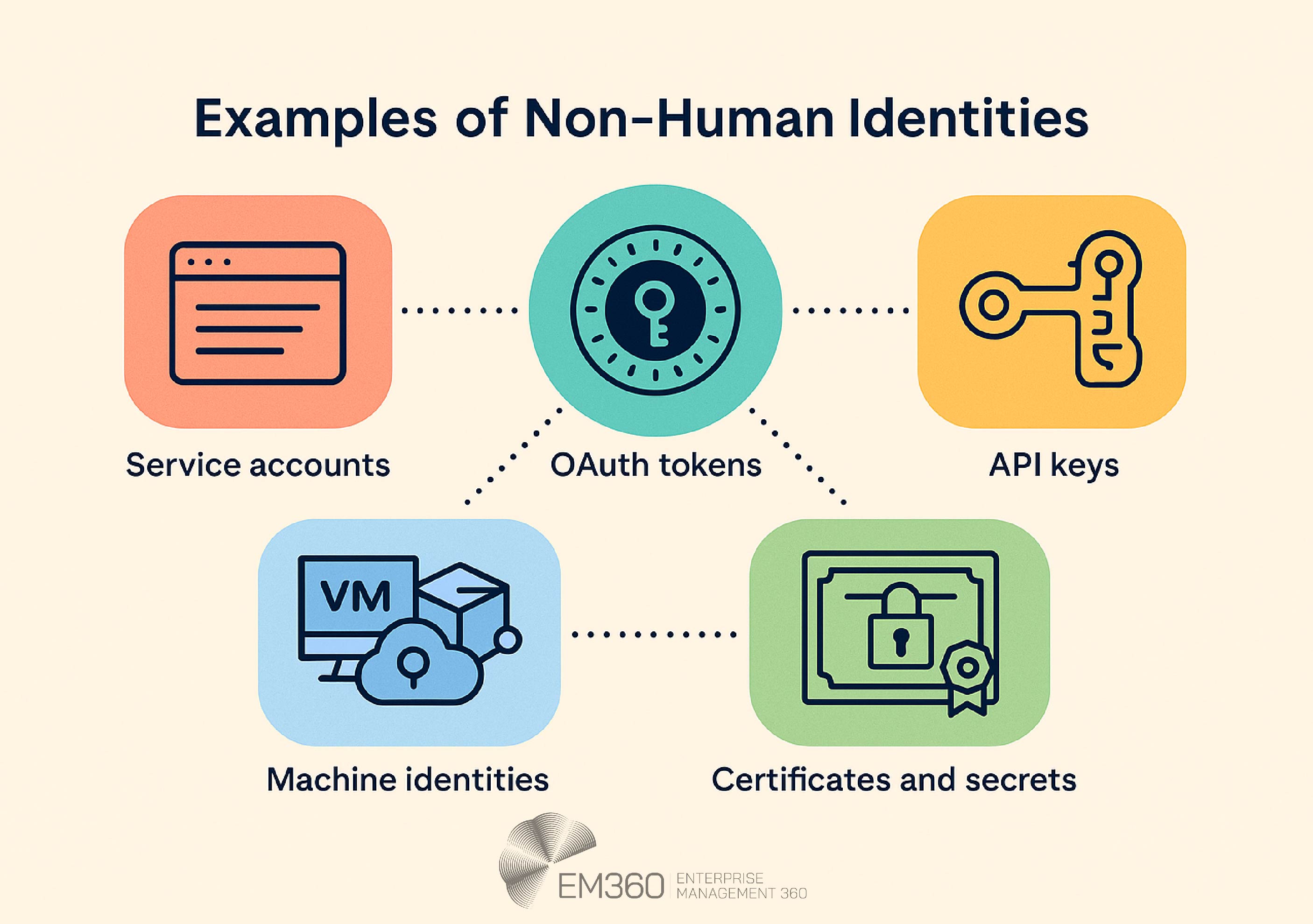
Non-human identities take many forms across enterprise architectures. Some of the most common include:
- Service accounts: Used by applications to interact with databases, internal services, or scheduling tools.
- OAuth tokens: Allow delegated access for applications to interact with external APIs without exposing user credentials.
- API keys: Provide programmatic access to cloud platforms or microservices, often embedded in code or containers.
- Machine identities: Assigned to devices like virtual machines, containers, and IoT endpoints so they have the needed authority for trusted communications.
- Certificates and secrets: Authenticate encrypted sessions between machines or authorise cloud-based automation.
These identities power everything from CI/CD pipelines and cloud workloads to IoT ecosystems and robotic process automation (RPA) bots, which makes them foundational to modern enterprise operations.
Human vs Non-Human Identities — What’s the Difference?
Most organisations treat human identities and non-human identities as part of the same access management strategy. But that’s a mistake. These two identity types behave very differently, and so do the security risks they introduce.
Authentication and interaction
Human identity security is built around user behaviour. People authenticate themselves using passwords, biometrics, or mobile-based MFA, and then interact with systems through user interfaces or applications. They can be prompted to verify, challenged if behaviour changes, or locked out if credentials are compromised.
Non-human identities don’t follow the same rules. A machine identity, like a container, microservice, or virtual machine, uses various digital methods to authenticate itself in the background without anyone needing to be involved. These identities don't use things like MFA or single sign-on (SSO), and they don't respond to prompts.
Once they get their credentials, they usually stay the same and aren't watched unless there's a specific policy for NHIs in place for your organisation.
Lifecycle and ownership
Human users typically go through defined identity lifecycle stages — onboarding, role changes, offboarding — with corresponding updates to their access rights. They’re assigned to a manager or HR contact. Their accounts are reviewed as part of regular audits.
Non-human identities rarely follow that same structure. Most are generated automatically as part of automated processes like when an API is provisioned, a new cloud function is deployed, or a DevOps pipeline spins up a temporary workload. Many are created without formal ownership, documentation, or expiration dates.
That lack of visibility adds up. According to industry research, only 5.7 per cent of organisations can fully inventory their non-human identities. And without proper tracking, governance, or credential rotation, these invisible entities become long-term vulnerabilities.
The Hidden Security Risks of Non-Human Identities
As automation increases, so does the attack surface. Non-human identities are essential to cloud operations and DevOps workflows. But they’re also creating thousands of potential entry points that most organisations can’t see, let alone secure.
Scale and sprawl
Most non-human identities aren’t created with long-term oversight in mind. They’re generated automatically by systems, scripts, and services; and they often persist long after their original purpose has passed. The result is identity sprawl, where old credentials pile up and unauthorised access becomes easy to miss.
It’s not just about volume. Many of these identities are over-permissioned from the start. Some are never rotated. And without routine access reviews or automated expiry policies, they become ideal targets for attackers looking to move laterally or escalate privileges.
Real-world breaches and attack vectors
These aren’t theoretical risks — they’re already being exploited. In the past year, 46 per cent of organisations confirmed non-human identity–related breaches. And many more suspect there are issues they simply haven’t detected yet.
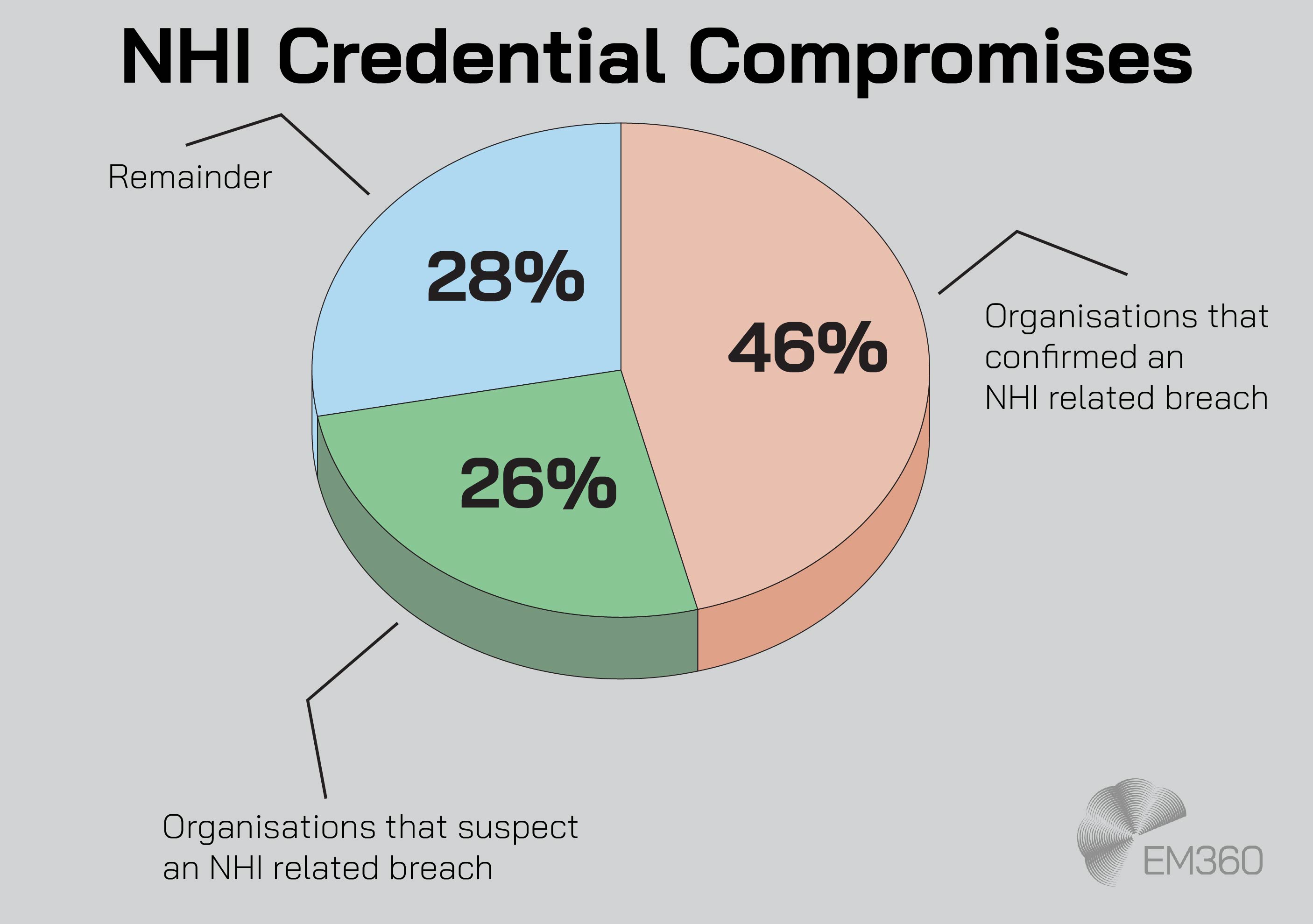
One of the most common weaknesses is poor secrets management. Static credentials like API keys, tokens, or embedded passwords often end up hardcoded in public repositories, shared scripts, or cloud environments. It’s why “Secret Leakage” ranks as the second-highest threat in the OWASP Top 10 for NHIs.
Breaches at the New York Times, Toyota, and the US Treasury have all been traced back to this kind of exposure. In each case, compromised machine credentials gave attackers a silent way in — bypassing traditional controls and putting sensitive information at risk.
How NHIs Fit into Modern Identity Security Strategies
Most organisations have a strategy for managing human access — onboarding, SSO, role-based permissions, and multi-factor authentication. But non-human identities don’t fit neatly into those systems. They’re operating outside the traditional models, and the tools used to protect them haven’t kept pace.
Why traditional IAM tools fall short
Identity and access management (IAM) platforms are built around people. They assign roles, enforce logins, and track sessions. But non-human identities don’t behave like human users. They don’t sign in, rotate credentials on their own, or respond to challenges like MFA.
That’s where the gaps begin. Most NHIs are invisible to standard IAM dashboards. They’re not subject to password policies or lifecycle triggers. And even where access controls exist, they’re often manually configured or inconsistently enforced. Without built-in monitoring or automation, it becomes impossible to govern them at scale.
As machine identities proliferate, these blind spots create real operational risk. Especially when static credentials are shared between systems, embedded in code, or left untracked in multi-cloud environments.
Aligning with Zero Trust and regulatory frameworks
Security teams are increasingly looking to Zero Trust models to close those gaps. Instead of assuming trust based on perimeter or system, Zero Trust treats every identity — human or otherwise — as untrusted by default. That means every access request must be verified, context-aware, and time-limited.
For non-human identities, this involves applying policies like least privilege, continuous validation, and credential scoping at the machine level. Secrets should be short-lived, access should be logged, and identities should expire unless revalidated.
This approach also supports compliance mandates that now explicitly reference non-human access. Frameworks like PCI DSS, ISO 27001, and SOC 2 all require organisations to manage and audit every identity with access to sensitive data. Not just human ones.
Despite this, research shows that fewer than 15 per cent of organisations feel confident in their ability to secure non-human identities. That confidence gap isn’t just a technology problem, instead it’s a visibility and governance problem. And it’s one that modern identity strategies will need to close.
Best Practices for Managing Non-Human Identities
Non-human identities aren’t going away and neither are the risks they introduce. But with the right visibility, policies, and automation, they can be brought under control. These best practices form the foundation for securing NHIs at scale.
Build a complete inventory
You can’t protect what you can’t see. Identity discovery is the first step in securing non-human access, but it’s also one of the hardest. NHIs are often scattered across cloud platforms, embedded in scripts, or buried in pipeline configurations. Many don’t have clear owners and some were never meant to be long term.
A complete inventory should cover every type of machine credential, from service accounts and OAuth tokens to certificates and container identities. The goal is to understand where they exist, what they can access, and whether they’re still in use.
To get there, security teams should use agentless discovery tools and integrate with cloud infrastructure entitlement management (CIEM) platforms that can continuously map machine access across environments.
Apply the principle of least privilege
One of the most common causes of NHI-related breaches is over-permissioned access. It’s easy to assign broad privileges to a service account or API key just to get something working, but those permissions often go unreviewed for months, or even years.
Applying the principle of least privilege means giving each identity only the access it needs, for only as long as it needs it. That might mean using role-based access controls (RBAC), segmenting access by environment, or enforcing time-bound credentials for automation tasks.
Where possible, long-lived tokens should be avoided. Secrets should expire automatically. And ephemeral credentials like short-term OAuth grants or workload-based tokens should become the default.
Monitor and audit continuously
Even the most carefully scoped access can become risky over time. That’s why real-time monitoring and continuous auditing are critical to NHI security. Every machine identity should have its behaviour baselined and monitored for anomalies — from unexpected privilege escalation to unusual access patterns across systems.
Policy-based automation can help here. Security tools should be able to detect when a credential is used in an unfamiliar context, trigger alerts, and automatically revoke or rotate access if something goes wrong. Regular access reviews, automated expiry, and audit trails are all essential to keeping risk in check.
The Trends Shaping the Future of NHIs
As enterprise environments evolve, so does the identity landscape. The trends shaping non-human identities aren’t just about scale; they’re about how organisations define trust, authority, and access in increasingly automated and distributed systems.
Rise of AI and autonomous agents
The emergence of agentic AI is pushing the boundaries of identity even further. These aren’t just bots running predefined scripts — they’re systems capable of decision-making, delegation, and adaptive behaviour. As their role in enterprise workflows grows, they’ll need to authenticate against APIs, services, and cloud platforms using dedicated credentials.
That presents a new challenge. Identity management must now account for digital entities that act independently and interact with infrastructure in unpredictable ways. Some researchers have already started referring to them as virtual employees, highlighting the shift from task execution to autonomous participation.
Cloud-native and multi-cloud complexity
Cloud adoption has already expanded the machine identity surface. But it’s the rise of containers, ephemeral workloads, and multi-cloud orchestration that’s driving volume and fragmentation at speed.
Each time a container launches or a serverless function is invoked, a new non-human identity is created. Most are short-lived, but they often hold broad access while they’re active. Without proper controls, they leave behind unmonitored access paths and stale credentials.
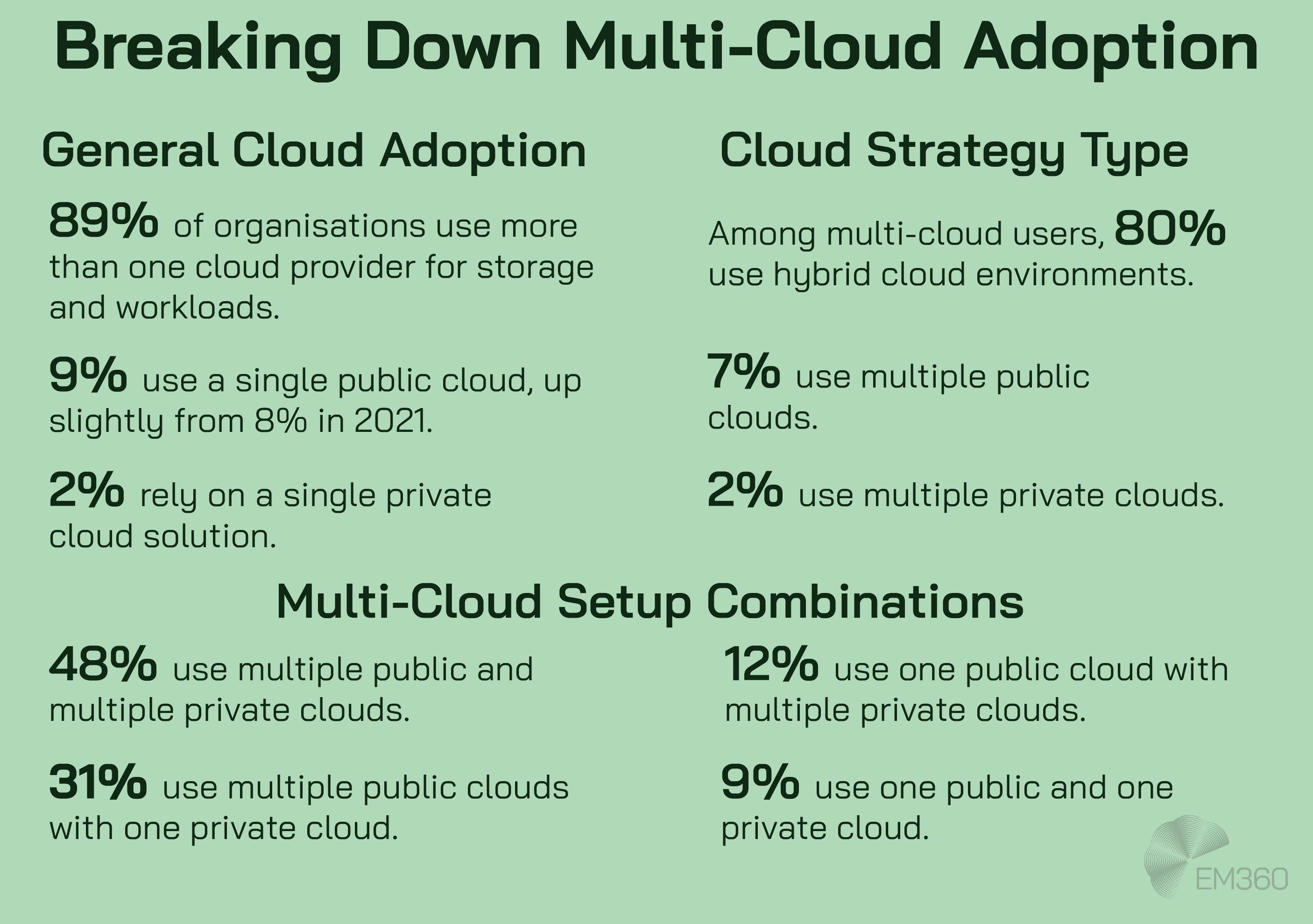
It’s estimated that enterprises will see a 100 to 1 ratio of non-human to human identities in 2025, and that will only increase in the future. That shift turns NHIs from a niche concern into the dominant source of identity-related risk.
Final Thoughts: NHIs Deserve a First-Class Security Strategy
Non-human identities aren’t a side issue. They’re not just a DevOps detail or a cloud configuration concern. They’re a foundational part of modern enterprise infrastructure, and the systems they connect are often the ones that matter most.
From machine learning pipelines to infrastructure as code, NHIs power the automation that businesses rely on to move faster, scale smarter, and operate globally. But without strong identity security measures in place, they also introduce some of the most overlooked and easily exploited gaps in today’s cybersecurity posture.
A first-class security strategy means giving NHIs the same visibility, governance, and protection already in place for human access. That starts with inventory and access controls, but it also includes automation, behavioural monitoring, and alignment with frameworks like Zero Trust.
The organisations that get this right won’t just reduce risk — they’ll create a more resilient, future-ready identity ecosystem. And as the identity landscape continues to evolve, EM360Tech remains a trusted space for exploring how enterprise leaders are navigating identity security, automation, and Zero Trust in practice.











Comments ( 0 )